The trouble with compromised email accounts and how to keep yours secure
 Scammers continually target potential victims with phone calls, letters, text messages, emails, and more. Phishing email scams are especially common, by some estimates accounting for 1% of all email traffic.
Scammers continually target potential victims with phone calls, letters, text messages, emails, and more. Phishing email scams are especially common, by some estimates accounting for 1% of all email traffic.
Phishing emails can lead to the loss of important personal information, including the possibility for a compromised email account. When this happens, the scammer has access to more than just your email.
Think of your email inbox like your wallet. You use your email account to reset passwords, access your online banking and social media accounts, and more. If a scammer has access to your account, they have access to every kind of personal information associated with that email address.
The SLAM method
Golden West strives to give you the best tips and information to protect you and your online accounts. At first glance phishing emails can appear legitimate, so it’s important to learn to identify phishing messages to keep yourself and your accounts safe. A great tool for doing this is the SLAM method, which stands for Sender, Links, Attachments, and Messages.
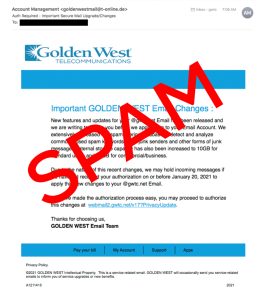
![]() S = Sender. Look closely at the email address from which the message was sent – not just the display name. For example, a previous phishing message that appeared to be from Golden West showed a display name of “Account Management,” but the message was sent from “goldenwestmail@t-online.de” as the email address. Stay away from messages that come from an unfamiliar email address; do not trust the display name.
S = Sender. Look closely at the email address from which the message was sent – not just the display name. For example, a previous phishing message that appeared to be from Golden West showed a display name of “Account Management,” but the message was sent from “goldenwestmail@t-online.de” as the email address. Stay away from messages that come from an unfamiliar email address; do not trust the display name.
![]() L = Links. Scrutinize the links within an email message. If a link is unrecognizable, don’t click on it. If the displayed link doesn’t match where the link leads or the link may be hiding alternate characters, don’t click on it. Hover over a display link (without clicking on it) to see the actual URL to which the link leads to determine if it’s authentic or suspect.
L = Links. Scrutinize the links within an email message. If a link is unrecognizable, don’t click on it. If the displayed link doesn’t match where the link leads or the link may be hiding alternate characters, don’t click on it. Hover over a display link (without clicking on it) to see the actual URL to which the link leads to determine if it’s authentic or suspect.
For example, the Golden West link is “https://www.goldenwest.com.” A scammer may send you a link with other characters, such as “https://www.g0idenw3st3.com” or something even harder to distinguish like “https://www.g01denwest.com.” Avoid clicking on links inside emails and instead, visit the site directly by typing goldenwest.com into your browser.
![]() A = Attachments. Don’t open any attachments except those you are expecting to receive. Clicking on unfamiliar attachments may install malware, such as viruses or spyware, on your device.
A = Attachments. Don’t open any attachments except those you are expecting to receive. Clicking on unfamiliar attachments may install malware, such as viruses or spyware, on your device.
![]() M = Message. Double check the body of the email for odd language or typos, along with anything that seems off about the message. Grammar and spelling errors are signs of a phishing message. Those that appear to come from Golden West sometimes misuse the name as “Goldenwest” in one word, for example.
M = Message. Double check the body of the email for odd language or typos, along with anything that seems off about the message. Grammar and spelling errors are signs of a phishing message. Those that appear to come from Golden West sometimes misuse the name as “Goldenwest” in one word, for example.
Password protection tips
Another repeated tip that’s not taken seriously enough is to use long, strong, and unique passwords. Many people use the same password for all accounts. Golden West advises you to use alternate passwords for each account.
Passwords can be stored in a password manager, on a hard drive, or kept somewhere safe. Use 12 characters for your password – 16 is even better – with a mixture of upper- and lower-case letters, numbers, and symbols.
At first glance phishing messages may look real as they often contain Golden West logos that have been copied from another online source. Look closer for inaccuracies and red flags. These messages also may request login credentials, and Golden West will never require you to update account information from an email.
Scams can be costly
A compromised email account is a huge security issue. It can lead to a loss of personal information, including banking and credit card information, social media logins, passwords, and more. This puts your reputation at risk and could also cost you money. Worse still, resolving the issue could take hours, days, or months.
Thankfully, pausing before acting on email requests and following the SLAM method to verify email can help protect you.



